Networking Fundamentals
As a student exploring cybersecurity, I’m always hearing that getting a grasp of networking fundamentals is essential for any branch.
From a penetration testing environment, protocols can commonly be pathways for breaking into systems and doing harm. For example, the relatively EternalBlue exploit took advantage of the Server Message Block (SMB) protocol on port 445 in Windows 7 and 8 devices and allowed attackers to gain root access to those machines.
From a cloud perspective, most Infrastructure as a Service (IaaS) platforms like Azure, AWS, Oracle Cloud, etc allow customers to reproduce on-prem capabilities through features such as virtual networks, DNS hosting services, firewalls, and many more.
In digital forensics, scientists often reproduce network traffic between devices, distinguish erratic network traffic flows from normal ones, and copy data across devices in order to utilize them as evidence in cases.
These fundamental ideas influence everything, really. Nevertheless, with that breadth of application comes a breadth of knowledge necessary to nurture a solid cybersecurity foundation. Using TCM Security PEH course as a guide, here are some great foundational subjects that I’ve been trying to familiarize myself with.
IP Addresses
Suppose you have two devices, say Ti and Cee, who are housemates and want to communicate with each other through a local network. The first thing they need to do is somehow identify where they are located. To do this, they go to the Router and ask for a tag for each of their rooms. The Router says “sure” and then assigns each of them an IP Address, a unique decimal identifier characterized by 4 octets, or 32 bits, to put on their doors.
Ti is assigned the IP Address of 192.168.146.1 and Cee is assigned the IP Address of 192.168.146.2.
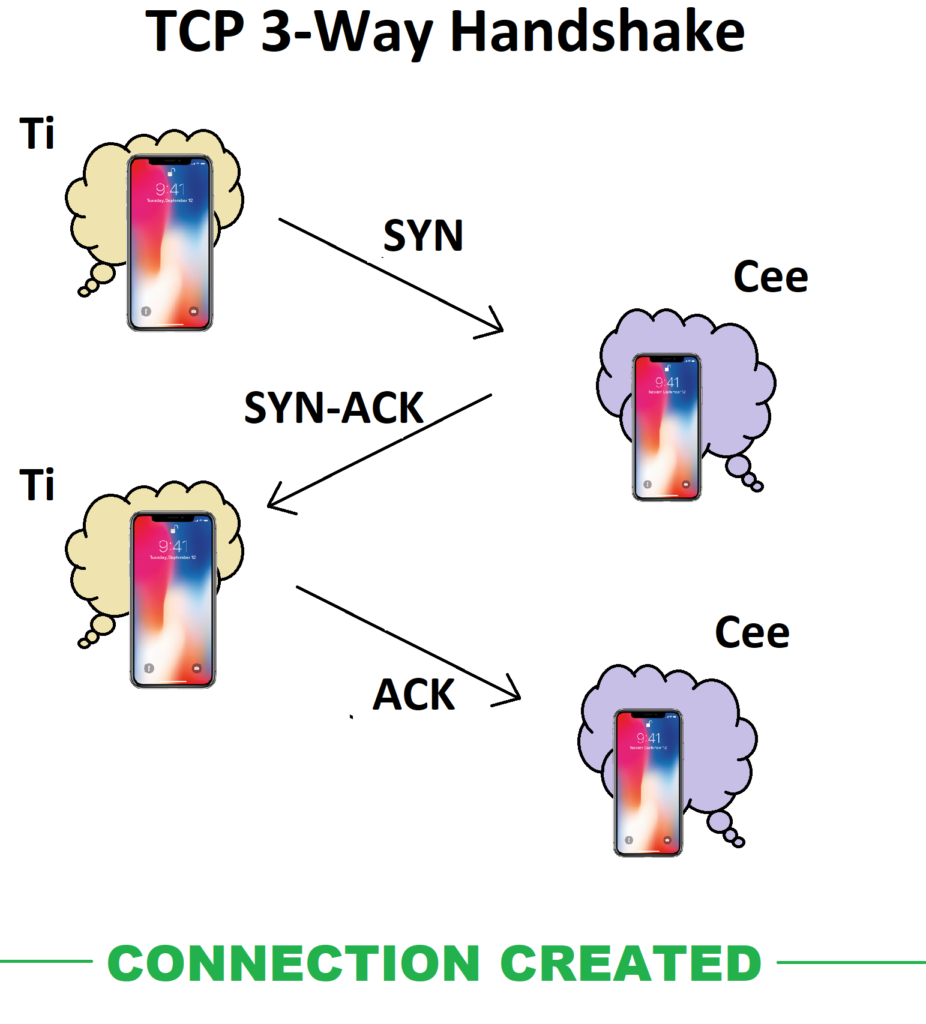
Great! Now, they can tell whose room is whose, but they’re super best friends and don’t want to share any secret, spicy messages without making sure that the other device is at the end to receive them. As a result, Ti and Cee follow the TCP (Transmission Control Protocol) in order to make sure that they can reliably reach one another through a method called the Three-Way Handshake.
- Ti sends a “SYN” message packet at Cee’s to make sure Cee is available.
- Cee returns Ti a “SYN-ACK” acknowledgment message packet back to Ti’s door to say that Cee is indeed available and also checks again if now is also a good time for Ti to communicate.
- Ti sends in a “ACK” message packet to confirm the connection
Now, whenever they communicate, the connection carefully ensures that packets are received reliably and orderly. If one device doesn’t receive an acknowledgment from the other within a certain time frame, it resends the packet to ensure that all the data is delivered properly.
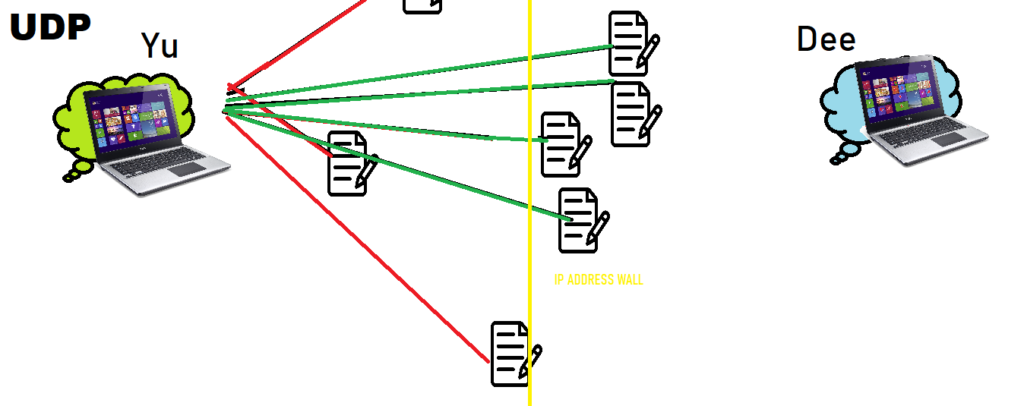
Suppose we have two other devices, Yu and Dee, who are also housemates and also want to communicate with one another. Similar to Ti and Cee, the Router gives them both an IP address for their rooms.
However, in this case, Dee is cramming for an exam last second and can use really any sort of help that Yu can provide. Yu is also busy with its own things, so Yu decides to catapult whatever notes it has in the direction of Dee’s door. Some notes might get lost, but Dee doesn’t mind since information gets sent quickly. This follows the UDP (User Datagram Protocol) type transaction.
What if one housemate moves to a different house, but still wants to maintain their communications over the internet. Luckily for them, the Routers in each of their houses can use Network Address Translation (NAT) to create a public IP for outgoing communication. When the Routers receive the messages, they can then check the message headers to see the destination room for the message and deliver the packets to the appropriate recipient.
Subnetting
Sometimes communication can cause some really messy issues. Imagine if Ti, Cee, Yu, and Dee were all talking with one another, on top of 200 other devices in the same network. This would make distinguishing devices much more difficult in various cases. This is where subnetting comes into play!
Sub networks, or subnets, are smaller networks that compose the larger, main network and by dividing off certain networks, the following benefits are found, amongst many others:
- Management: Certain devices can be placed into certain subnets and this helps distinguish certain groups of devices from one another. Additionally, certain permissions can be granted to certain groups of devices based on subnets.
- Performance: Now that groups of devices, and consequently the device themselves, can be more easily identified by their subnet, receiving and sending communication becomes much more efficient!
- Security: Exploits and vulnerabilities can be isolated down to the subnet level which allows enables taking more specific protection measures without investigating perhaps the entire network
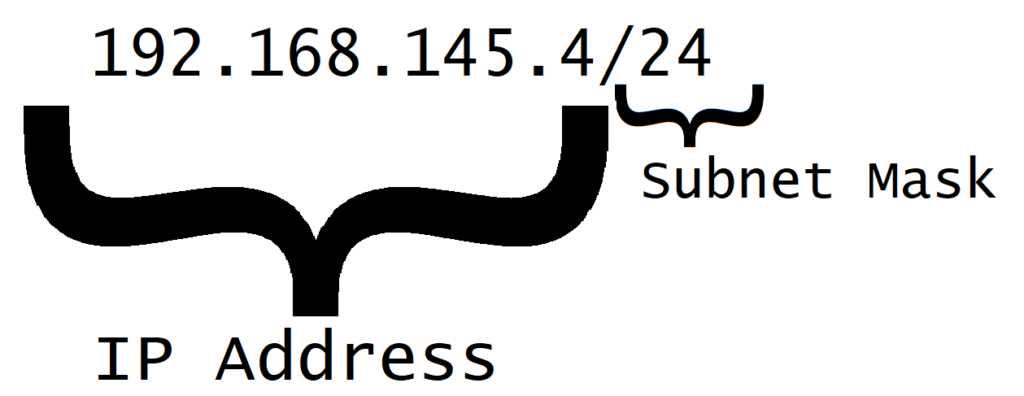
So how does subnetting work? For this, we should start off with two things: an IP address network and a subnet mask.
- 11111111.11111111.11111111.00000000 = 255.255.255.0 = /24
- 11111111.11111111.11111111.11111100 = 255.255.255.252 /32
- 11111111.11111111.11000000.00000000 = 255.255.192.0 /17
- 10000000.00000000.00000000.00000000 = 128.0.0.0/1
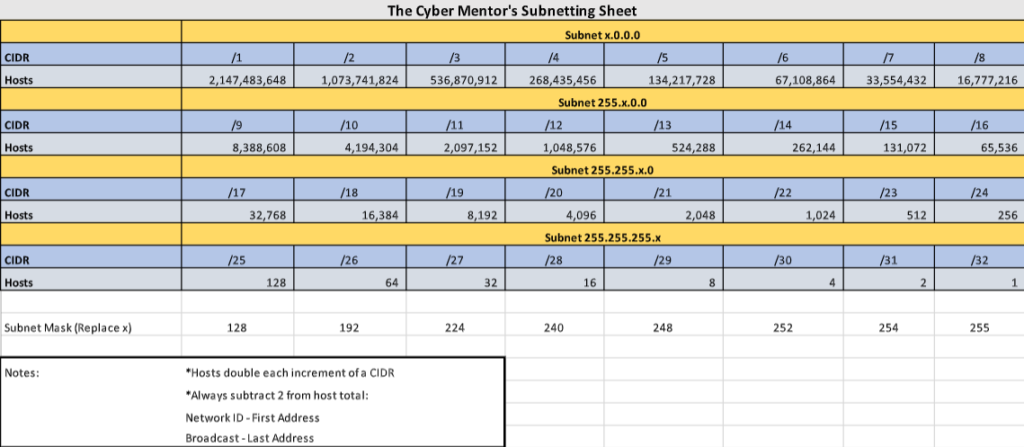
The CIDR notation translated form also provides two other key pieces of information. Given the number of network bits, say x, and host bits, say y, we can calculate the following:
- Block size of each subnet –> 2^y
- The number of total usable hosts per subnet –> 2^x – 2 (The first address of the total IP Range is dedicated as the Network ID and the last address is dedicated to the Last Address)
Take a look at our original IP address again, 192.168.145.4/24, with the above chart in mind. Then, we know that there are 8 bits dedicated to the host. This means that the IP can be split into 256 (2^8) subnets and additionally, that there are 254 total usable hosts (2^8 – 2). If we have something like 192.168.145.4/24 and 192.168.150.4/24, we know that these are two different subnets. However, say we had 192.168.145.4/20 and 192.168.150.4/20. The corresponding subnet mask is 256-240 = 16, meaning that the subnets of the network are split into blocks of 16 in the third octet (0-15, 16-31 … 240-255). Therefore, 192.168.145.4/20 and 192.168.150.4/20 would be in the same subnet since the start of that particular subnet block is 143.
0 Comments