SAP Cybersecurity Virtual Internship
Earlier this fall, SAP, a multinational software company, released their Cybersecurity Virtual Internship in partnership with Forage. Without a doubt, SAP places a great emphasis on security solutions, ensuring that their customers have access to key services like security information and event management (SIEM), on-prem and private cloud application security, active logging, analysis, and threat detection, to name a few. To say the least, I was very curious to discover which of the plentiful topics they would choose to introduce to their audience.
Meet Hoolie!
Task 1: Protect the keys to the kingdom!
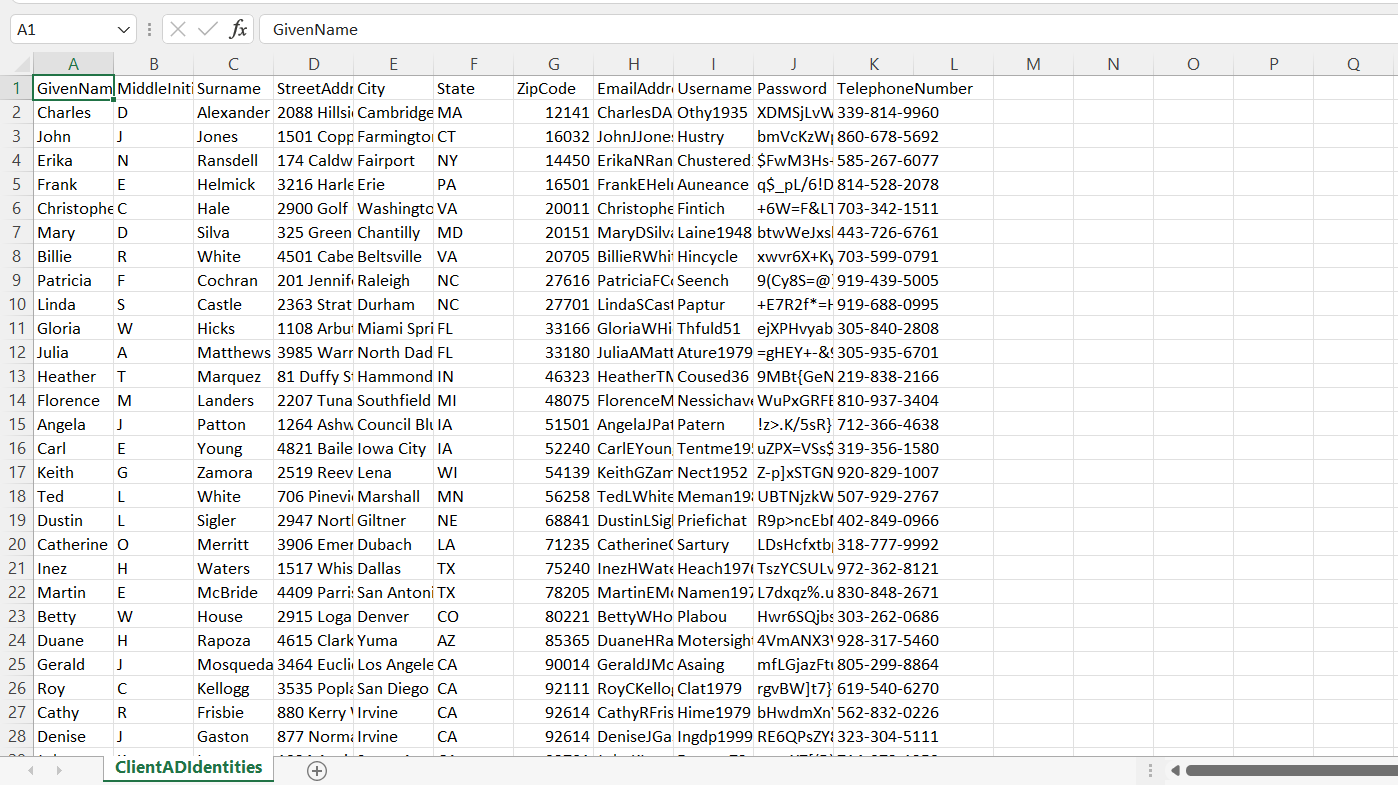
In the first task, we are introduced to Hoolie, a client that has been climbing their way up the ranks and consequently, now risks a higher chance of ransomware attacks. Ransomware is a certain type of malware where a cybercriminal holds data hostage through encryption and demands some sort of payment for the data to be recovered. In Hoolie’s case, criminals may put in more effort to crack employee passwords and gain elevated access to significant information like business plans, personal identification, or even methods to shut down services. We as humans especially tend to choose simpler passwords because they’re easier to memorize and despite most credential requirements enforcing rules like having 1 capital and lowercase letter, a number, a special character, etc., most people still tend to add on the bare minimum (like adding 1! or 123! at the end or capitalizing just the first letter). To help mitigate this, SAP provides references NIST recommendations on handling digital identities and additionally supplement a list of stronger password guidelines:
- Allowing only authorized applications to run only on authroized computers
- Minimum of 12 characters
- Not being a dictionary word or proper name
- Not being identical to any of the previous 10 passwords
- Not to being displayed when entered
- Ransomware Blocker
- Staying up to date with security updates
- Using Antivirus Software
Given these policies, we then had to verify that a group of Hoolie’s employees follow the password policy.
Task 2: Gone Phishing
Task 2 focuses on the risks of phishing emails, a sort of fake email that urgently insists the recipient to reveal personal information. Although it would seem apparent to not disclose any such information, phishing emails are so effective precisely because they can convince recipients that they are from trustworthy sources. For example, the sender may have an email from a recognizable domain or may pretend to be written by a boss or supervisor. This can become very dangerous, especially when aimed directly at high-ranking administrators, executives, and other powerful employees who may be coerced into revealing information that poses strategic risk. Avoid such emails:
- Emails with unrelated or random hyperlinks (hover over them to see their reference destination)
- Emails with mysterious or arbitrary senders or co-recipients
- Emails sent at unexpected times (for example, at like 2am in the morning on a Sunday or outside of working hours)
- Email bodies/messages with apparent spelling/grammar mistakes
- Email bodies with threatening or overly insistent requests
While it is definitely important to be cautious of these sorts of emails, it is also integral to ensure that there aren’t any false positives, or legitimate emails that are flagged incorrectly. To reduce this likelihood, affirming real emails allows the email filter or algorithm to get a better indication of which sorts of emails should not be automatically deleted, blocked, or sent to spam.
Task 3: Hardening your system
Hoolie’s servers have crashed (oh no… although, It’s interesting to consider though how a breached password may have enabled a criminal to get access and purposely break down these servers) and now we must revamp a new one running Windows 2019. Our first initiative is to take a look at the security password policies and make sure this time around, we enforce ones that further diminish the risk of uncompliant passwords.
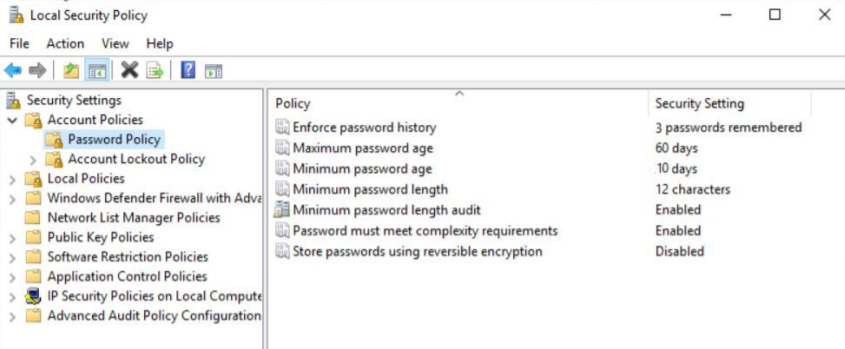
This task gave a glimpse into installing virtual machines and looking into directory permissions. We first download Oracle VirtualBox and an isolated image, or a file that contains all the installation files for a single program, for Windows 2019. Combining the two, we are left with an environment that allows us to configure the OS to our liking. We then search up “Local Security Policies” where the current rules are shown. They include:
- Enforce password history: number (from 0 to 24) of unique new passwords before an old one can be used
- Maximum password age: greatest number (from 0 to 999) of days before a new password must be set
- Minimum password age: least number (from 0 to 998 ) of days before a new password must be set
- Minimum password length: least amount of character a password must contain
- Minimum password length audit: creates an audit event whenever minimum password length is met
- Password must meet complexity requirements: if enabled, password must contain varied characters from at least 3 distinct categories: (lowercase letters, uppercase letters, digits 1-9, special characters, any other unicode character not including from within previous groups)
- Store password using reversible encryption: if enabled, allows passwords used for logging in and authentication to likewise be decrypted
For my password policy (for Hoolie, they had separate criteria in the first task), I wanted to generate one that stood in the middle ground in terms of security as this would probably best apply to most organizations. I kept the password history policy to 3, as SAP recommended in the lab because I figured that most people don’t actively use nor remember more than one or two passwords. While having those autogenerated random passwords stored in the browser can be convenient, I left that to be the 3rd choice in case a person doesn’t have an extra one or two passwords to consistently use. For the minimum password age, two months seemed to be reasonable because a person could cycle through their list of 3 passwords throughout the year and because the expiration age is more frequent, there is more opportunity to consider new passwords/signify password compliancy importance. The minimum age of 10 days would prevent any potentially breached accounts and the respective criminal from changing the password to their choosing. An influx of requests during this period could indicate suspicious activity. A minimum password length of 12 almost guarantees that dictionary attacks will not work and overall makes the password harder to crack. The complexity requirement being enabled additionally provides protection and variety. The password length audit provides insight into whether a minimum character count helps in the grander scheme of password security. And lastly, reversible encryption is disabled or else interceptors can very easily get information to that personal information.
Task 4: Final analysis and recommendations
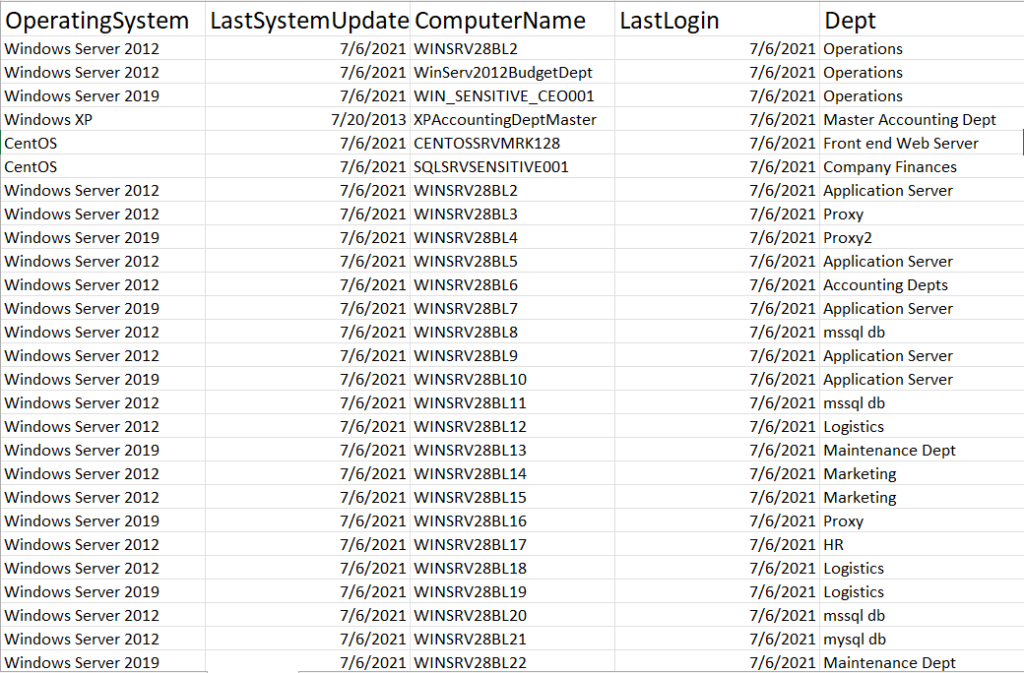
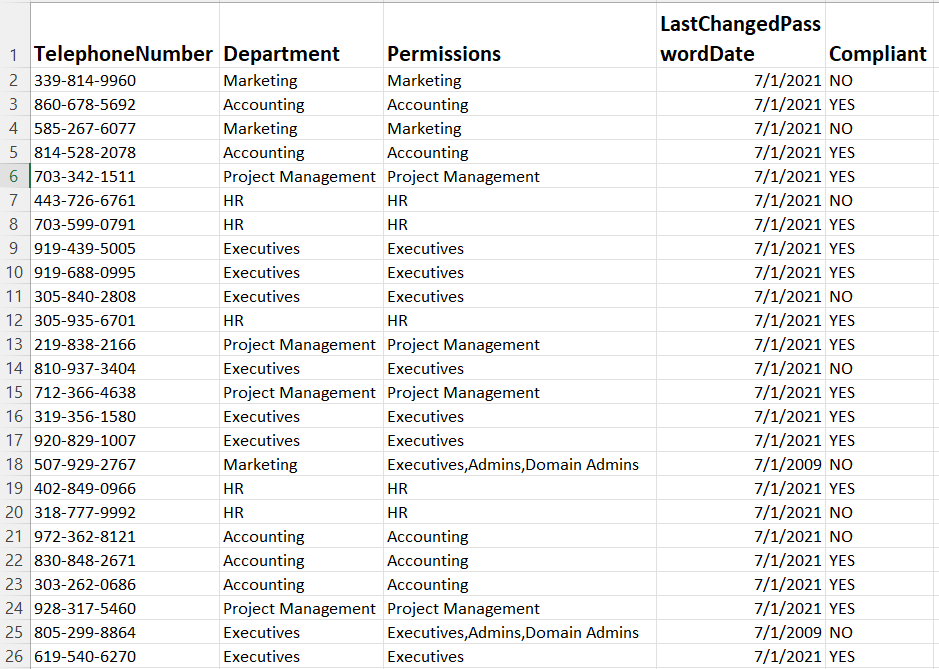
The last task encouraged us to take a deeper look into Hoolie’s employees, their departments, and permissions, & running systems/servers used by the company through a CSV log and figure out where potential vulnerabilities may arise. For the Sheet1 containing the first set of information, I focused on the users who had non-compliant passwords because exploits of their accounts induce a greater risk of valuable information getting stolen, held ransom, etc. Part of this was to look at their permissions and their distribution throughout the 5 listed departments. More frequency and points of vulnerability will inevitably lead to more windows of information leakage/hacks. Moving onto the Systems Sheet, I checked to make sure every server was up to date and supported by Windows. Additionally, I tried to make correlations between those who had non-compliant passwords and their departments to the departments that were using x, y, and z servers. If these users had administrative permissions and frequently accessed sensitive servers, this would increase the risk of important information becoming compromised.
Reflection
This virtual internship provided a gentle introduction into what cybersecurity at SAP could look like. A great emphasis was placed on password strength and compliancy which leads me to believe that despite increased password complexity requirements, this way of exploiting sensitive data is very much still a problem in the cyberspace. Similarly, SAP highlighted social engineering and phishing emails as another facet of accidentally putting sensitive data to risk. Overall, I would definitely encourage participating in this program to learn more about SAP and get a hint of the types of solutions they provide.




0 Comments