Posts
-
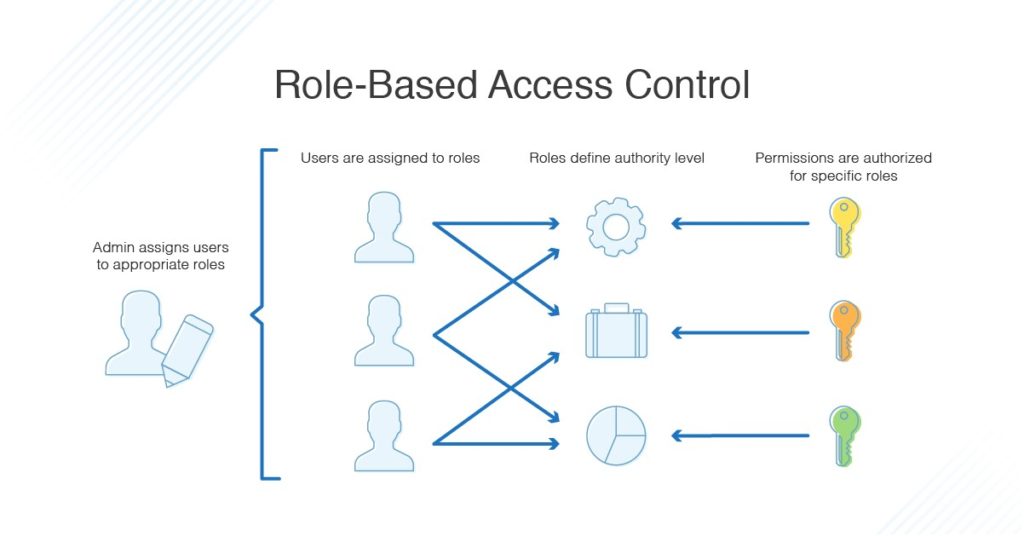
Azure RBAC/ABAC
Azure RBAC/ABAC Role-Based Access Control (RBAC) Role-Based Access Control (RBAC) is a key aspect of Azure Identity and Access Management and allows roles to be assigned to users to determine their permissions across different cloud hierarchy levels, ie management groups, subscriptions, etc. Additionally, it is generally recommended to assign roles on the higher hierarchal levels…
-

Azure Policy
Azure Policy An Azure policy is a rule that can be placed across management groups, resource groups, and resources to ensure that each respective environment is compliant with the organization’s standards. This means that real-time action can be taken against non-compliant areas, whether that be completely preventing their addition to the Azure environment, placing an…
-
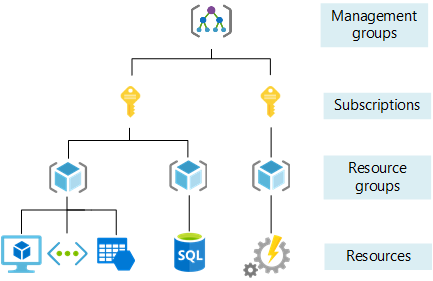
Azure Cloud Hierarchy
Azure Cloud Hierarchy Cloud governance is the rules, policies, and practices that help run an organization’s environment. This set of conditions helps an organization remain organized in several ways, from creating logical separations of resources across different departments to tracking costs in a more orderly manner to ensuring correct authorization and accessibility of user permissions.…
-

Passing the AZ-900
Passing the AZ-900 The Azure Fundamentals exam, or AZ-900, is Microsoft’s introductory certification into the world of the Azure cloud platform. Preparing for it gives one an overview of several key cloud computing concepts and general services, along with specifics that make Azure unique from its competitors such as AWS or GCP. A few topics…
-

Networking Fundamentals
Networking Fundamentals As a student exploring cybersecurity, I’m always hearing that getting a grasp of networking fundamentals is essential for any branch. From a penetration testing environment, protocols can commonly be pathways for breaking into systems and doing harm. For example, the relatively EternalBlue exploit took advantage of the Server Message Block (SMB) protocol on…
-
Upgrading to Larger SSDs
Upgrading to Larger SSDs Introduction Last year, I had the chance to grab a 16gb RAM stick and a 1TB SSD ROM and asked my friend B, a much more tech-savvy person than myself, to help me out with upgrading my laptop. Despite me asking, I kept procrastinating the upgrade, as something in my head…
-

Introduction to Nmap
Introduction to Nmap Nmap, short for Network Mapper, is an industry-standard for discovering different services and hosts. Oftentimes, it is used by hackers to find and exploit open ports that enable them to obtain access to sensitive data. This can lead to a strategic risk that can permanently damage the information and service integrity of…
-

SAP Cybersecurity Virtual Internship
SAP Cybersecurity Virtual Internship Earlier this fall, SAP, a multinational software company, released their Cybersecurity Virtual Internship in partnership with Forage. Without a doubt, SAP places a great emphasis on security solutions, ensuring that their customers have access to key services like security information and event management (SIEM), on-prem and private cloud application security, active…
